So, we have all probably heard about google Dorks. If not; it’s a technique where you use google and its search filters to search for very specific things / security holes. OffSec has a website dedicated to this technique: Google Hacking Database (GHDB).
I knew about them but never actually used then. So, over the course of a few days, I set a few hours aside to see what I could find. I used Offsec’s GHDB as a starting point and modified filters to my liking. To be honest; it was fun and way to easy to find interesting stuff. I played around with ‘confidential’ filters but didn’t find anything.
But then: Excel documents in wp-content/uploads containing passwords. This was by far the most result yielding path. Starting point:
inurl:wp-content/uploads filetype:xls | filetype:xlsx password
An Canadian IT news website hosted an excel document containing multiple passwords. I tested the LinkedIn account and it worked. This news website is very much into security (cause its cool) and even has an article advocating for responsible disclosure policy’s. Sadly, they didn’t have one and I was not able to find any contact form. I emailed their parent company and got a quick response.

Timeline
- 04/05/2022 17:25: Initial disclosure to news outlet’s parent company
- 04/05/2022 20:07: Response from news outlet. Thanks for reporting, file will be deleted shortly
- 04/05/2022 21:17: File has been removed
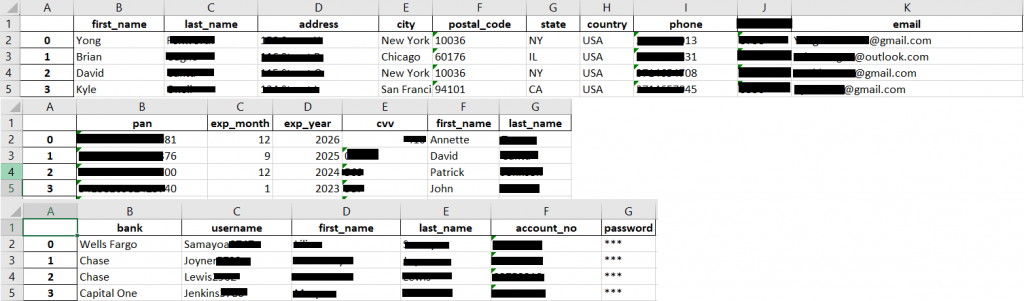
A credit card payment provider hosted a excel document containing 97 records. The document contains all the personal information you can think of, including social security numbers and credit card numbers including CVV code. Initially I though this was testing data, but the data looked random. Their documentation notes: all test data uses their own domain for mail addresses. This Excel document contained yahoo, outlook, Hotmail and Gmail addresses. I never found out if the document was legit (no reply), but the file has since been removed.
Timeline:
- 04/05/2022: Initial disclosure to vendor
- 12/05/2022: Second attempt due to no response
- 17/05/2022: Third attempt due to no response
- 29/05/2022: File has since been removed
Onto the next query, apparently you can search the blob.core.windows.net domain, starting query:
site:*.blob.core.windows.net ext:xls | ext:xlsx (login | password | username)
This yielded a huge password file. A marketing company did a campaign for a pest control company and leaked a excel document containing more then 100 usernames and passwords. Except of the leaking document part, this pest control company got its moneys worth. If you can think of a review website, the marketing company created an account!

In this document 1 email stood out because it was different from the rest: login information for Webflow (hosting company). Logging into Webflow I fully expect to be able to manage the pest control’s site. Boy was I wrong: upon logging in i was greeted by a dashboard containing all the marking company’s customers.
Timeline:
- 05/05/2022: Initial disclosure to vendor
- 12/05/2022: Second attempt due to lack of response
- 17/05/2022: Third attempt due to no response (including customer, personal and work mail)
- 29/05/2022: Fourth attempt due to lack of response (including customer(s), personal and work mail)
- 03/06/2022: Fifth and last attempt…
- 10/06/2022: As of writing files have not been removed
The blobs didn’t yield much more, onto the next one! Git repos. Starting query:
intext:"Index of /.git"
Initially I found a few boring repos until I stumbled upon an insurance company exposing a .git folder with directory listing enabled. I downloaded the .git folder: wget -r <url> and had a quick look of the code. It appeared to be the source of their front-end. A few passwords were found including the login to insurance @<company>.co and a URL to a back-end.

What if they made the same mistake on the back end? The back end gave a Forbidden, but can we still download the repo?
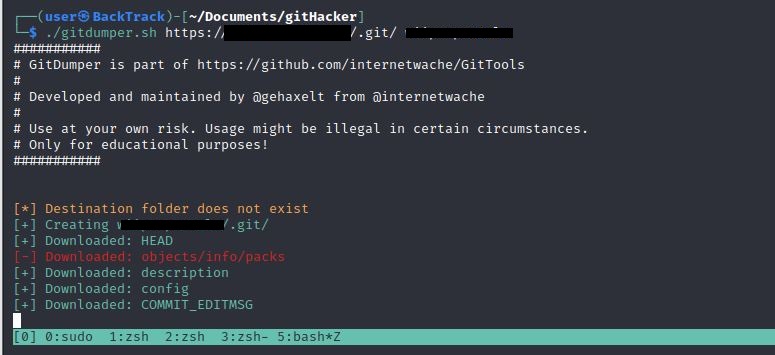
GitDumper is a cool tool to download .git folders if directory listing is disabled. GitDumper was able to download most of the repo:
After taking a quick look at the code it was time to inform the company. I tried, trust me, but never got a response.
Timeline:
- 06/05/2022: Initial disclosure to company (including parent company and web developers’ mails found in git)
- 12/05/2022: Second attempt due to lack of response (5 receivers of my mail)
- 17/05/2022: Third attempt due to lack of response (5 receivers of my mail)
- 29/05/2022: Call to their ServiceDesk (got reconnected a few times but no one spoke English)
- 29/05/2022: Call to their Fraud Desk (got reconnected a few times but no one spoke English)
- 29/05/2022: Third attempt after calling, this time in Spanish (yeaj for google translate?)
- 03/06/2022: Fourth attempt due to lack of response (7 receivers of my mail)
- 10/06/2022: As of writing the repo’s have yet to be removed.
I had lots of fun doing google dorks for once. I was honestly surprised at how quick it yields results. But I have to say, my main take away is that it is hard to do responsible disclosures for these finding. I had a few more findings but those are to boring to note here. They ended the same way as most of these: never got a response and the files are still available. 🙁
