So this is a weird one, during a discussion about port scanning with colleagues i showed them shodan.io. – beautiful website, check it out! I used the IP-range of an other educational institution. While browsing though the result we spotted a reception pillar accessible from the internet. Why?
This pillar appears to function as a route planner though the building, requesting appointments, requesting wireless quest accounts etc. The website didn’t really function, it was not supposed to be accessible, but some features worked. Browsing though the pages a JavaScript file was found divining a lot of API-endpoints:
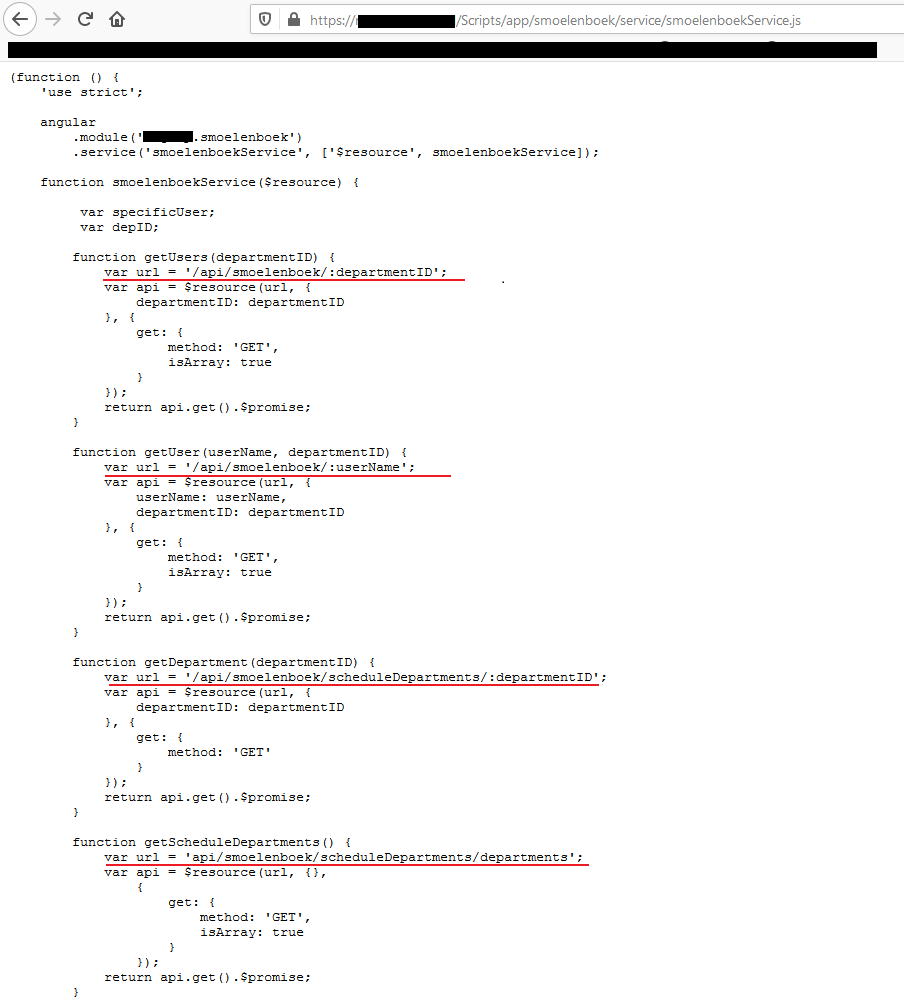
While playing around with these endpoints i noticed it was possible to request the details of a user. These details include the email of the user, password hash and salt:
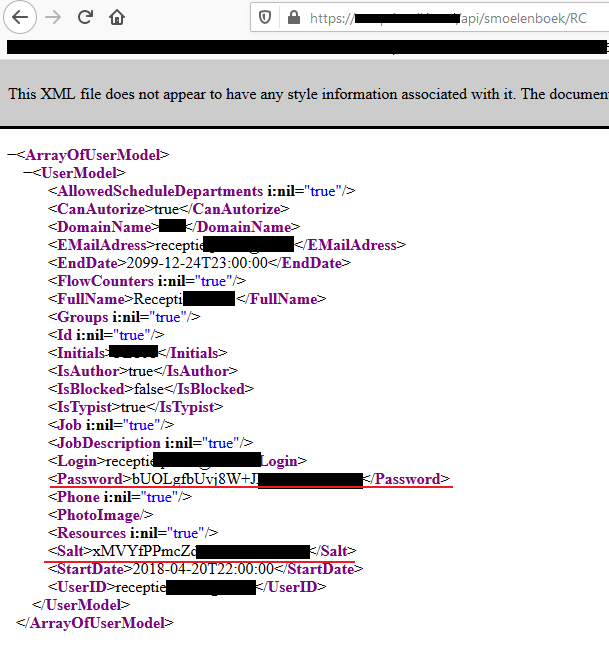
I informed the developer their software contained an information disclosure vulnarability and one of their customers was vulnerable over the internet. They were very adequate in there response!
Time line
- 22/01/2020: Initial disclosure to vendor
- 23/01/2020: Vendor acknowledged vulnerability
- 25/01/2020: A fix as been deployed & webpage removed from DMZ
- 27/01/2020: A phone call to thank me and goodies were received by mail a few days later
