So this is part of three vulnerability’s found over a longer period of time, the first one is reflected XSS. “Xerte is an award-winning suite of browser-based tools that allow anyone with a web browser to create interactive learning materials quickly and easily.” – https://www.xerte.org.uk. Xerte is an OpenSource project and can be found at: https://github.com/thexerteproject/xerteonlinetoolkits.
While browsing the code base i found the ability to print a project (https://<domain hosting Xerte>/print/). When printing a project the user has to provide the URL to their project and submit the request. The ?link= parameter is not checked and completely reflected on the webpage after submitting. Providing the following ‘link’ results in reflected XSS:
'></iframe><script>alert('XSS');</script>
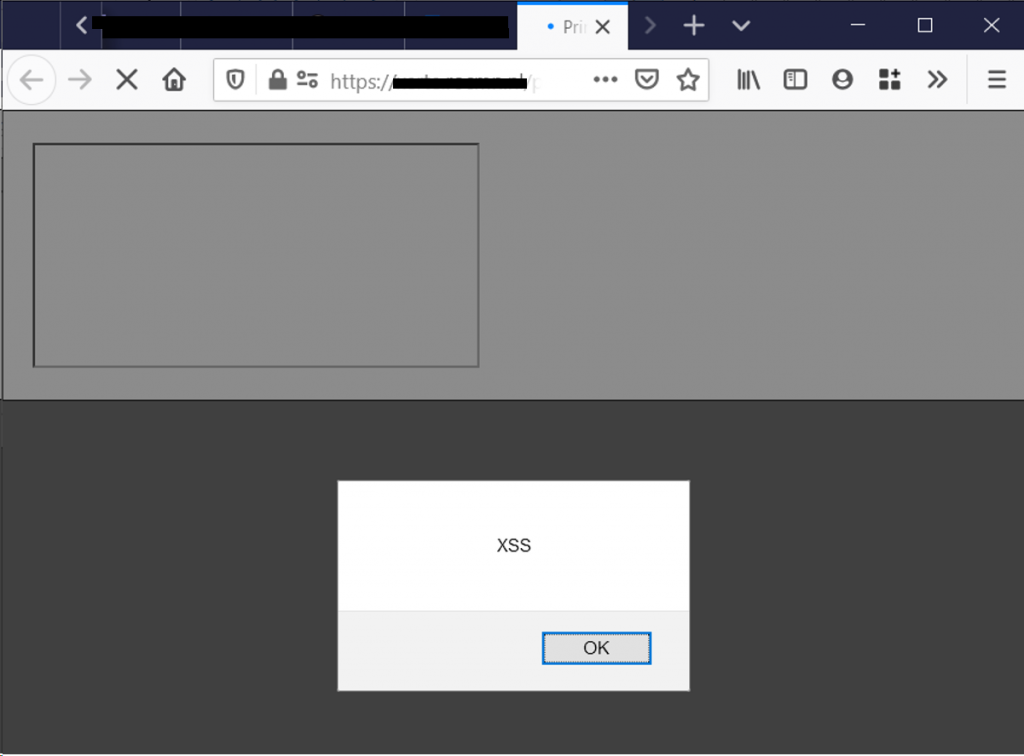
The presence of this vulnerability was successfully tested on six instances of Xerte.
Time Line:
- 16/03/2020: Initial disclosure to vendor
- 22/03/2020: Second attempt due to lack of response (also found unauthenticated RCE making it higher priority)
- 23/03/2020: Response from vendor
- 25/03/2020: Vendor acknowledges the problem
- 27/03/2020: Fix has been deployed
- 24/02/2022: CVE-2021-44662 assigned
